The sixth part of Azure Container Registry Unleashed is about scannig Docker Images in ACR using Azure Security Center. This post explains, what you get from Azure Security Center in the context of ACR and how to configure the integration of both Azure services. Before we dive into the article, I want to reach out and say thank you to my fellow MVP and well-known Azure security expert Tom Janetscheck for contributing to this article.
- What Is Azure Security Center
- Why Should You Use Azure Security Center
- Monitor ACR With Azure Security Center
- How Qualys Scans Your Docker Images
- Windows Docker Image Scanning
- Preview Features Worth Testing
- Conclusion
- The ACR Unleashed series
- What Is Next
What Is Azure Security Center
Azure Security Center (ACS) offers two main solutions. As a Cloud Security Posture Management (CSPM) solution, ASC constantly monitors the current configuration status of all your cloud resources and provides information to avoid misconfiguration regarding security. As a Cloud Workload Protection Platform (CWPP), ASC provides protection against cyber threats aimed at servers, no matter whether they are running in Azure, on premises, or in another cloud platform. It also offers protection against cyber threats aimed at your cloud-native workloads in Azure, such as Azure Key Vaults, Storage Accounts, AKS, SQL databases, and many more.
Why Should You Use Azure Security Center
First of all: because there is a free tier of Azure Security Center which offers the CSPM solution for your Azure-based workloads. By constantly determining the current configuration status and by reflecting the status in recommendations, you are informed if there are any misconfigurations to remediate.
In the standard tier, ASC offers even more capabilities such as monitoring cloud environments for regulatory compliance, or the threat protection capabilities, which make ASC the one stop shop for administrators who are responsible for deploying, administrating, and protecting (hybrid) cloud workloads.
Azure Security Center For ACR
ASC is also able to protect container-related Azure resources like Azure Container Registry. For ACR, every pushed image will be scanned for vulnerabilities and provide security recommendations using an external Docker image scanner offered by Qualys. Both vulnerabilities and security recommendations will be aggregated and classified directly in Azure Security Center UI. After a Docker image has been uploaded, it usually takes around 10 minutes to get scanning results back in ASC for your latest image.
Integrating with Azure Container Registry requires using the ASC Standard tier. Additionally, you will be charged per image scanning operation.
Monitor ACR With Azure Security Center
To enable the integration of ASC and ACR, you have to upgrade Security Center to the Standard tier. Go to Azure Security Center; you can change the tier using the Settings - Pricing Tier blade.
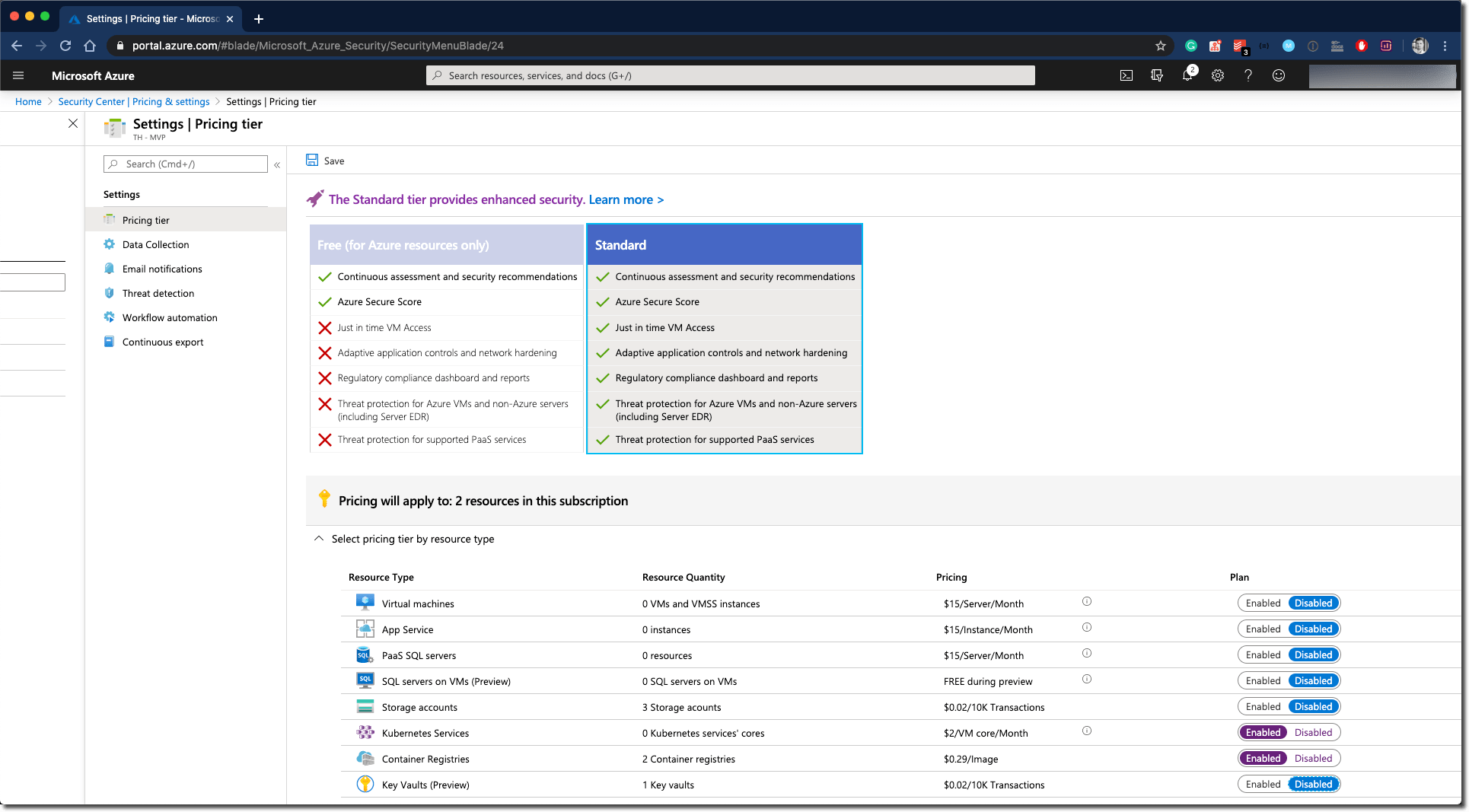
Once you have selected the Standard tier, you can enable the plan for the different resource types. Find Container Registries and enable it. Now, all your ACR instances will scan Docker Images and report vulnerabilities and security recommendations to ASC. (Don’t forget to hit Save, if you made some changes here).
Get Insights About Vulnerabilities In Docker Images
Once you have enabled the integration of ACR and ASC, you can push images to ACR. Qualys will scan your Docker Images now and report back into ASC. Use the Security Center UI to drill down through all findings of your Azure Subscription or Workspace to find ACR related recommendations. Security Center UI provides several dashboards that help you find the desired information in a manner of seconds. For example, go to Security Center - Resource Security Hygiene - Compute & apps, here you can filter all findings by resource category, set the filter to Containers and see all outcomes for services like ACR and AKS.
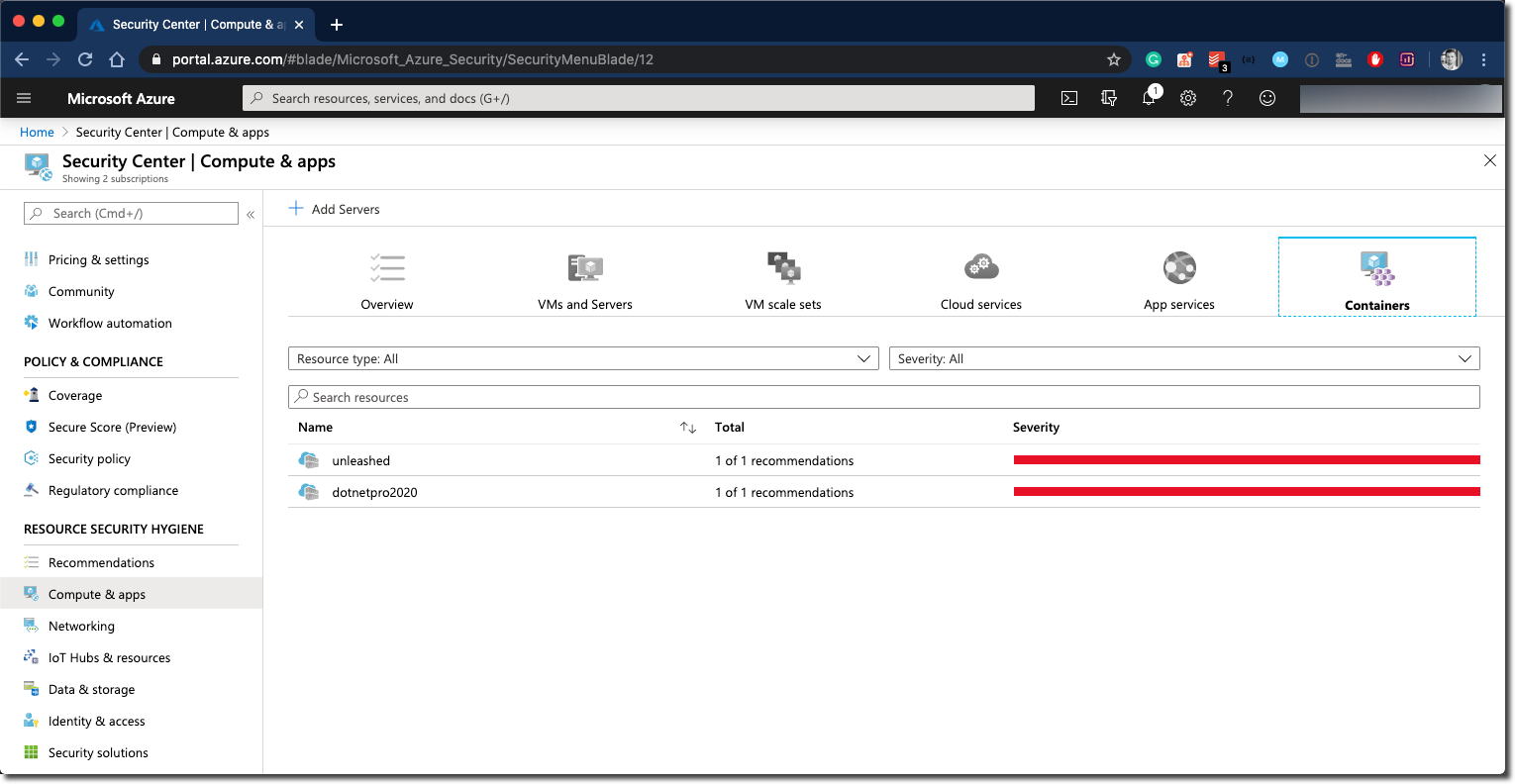
You can dive deeper from here, click the ACR instance you are interested in.
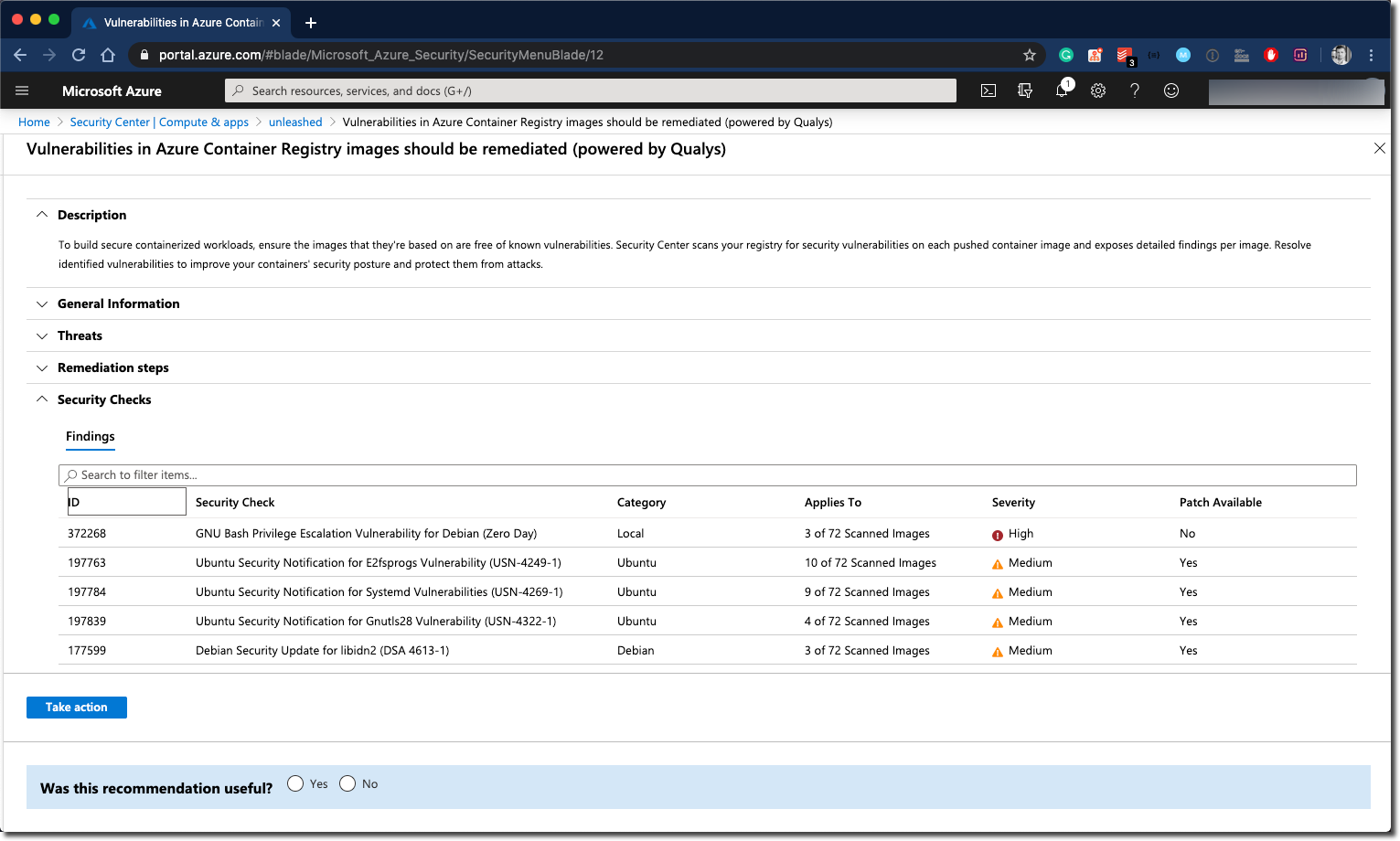
Did you notice the Take Action button below the list of findings? Following the button, you can get results per Image.
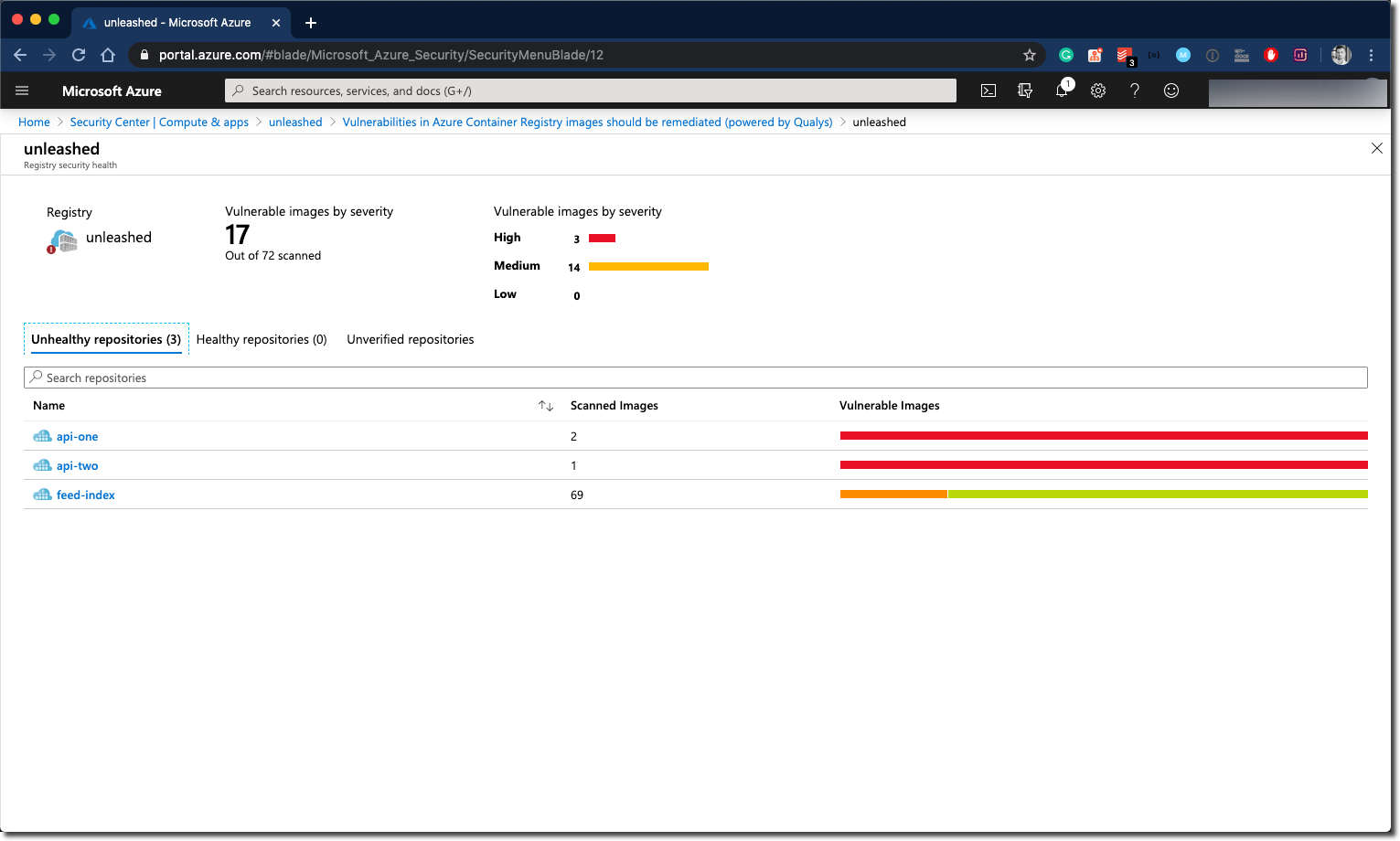
It doesn’t stop here; by clicking the image name, you will get a list of findings per Docker image tag, and finally, you get helpful information about the vulnerabilities/security recommendations and learn how to fix those.
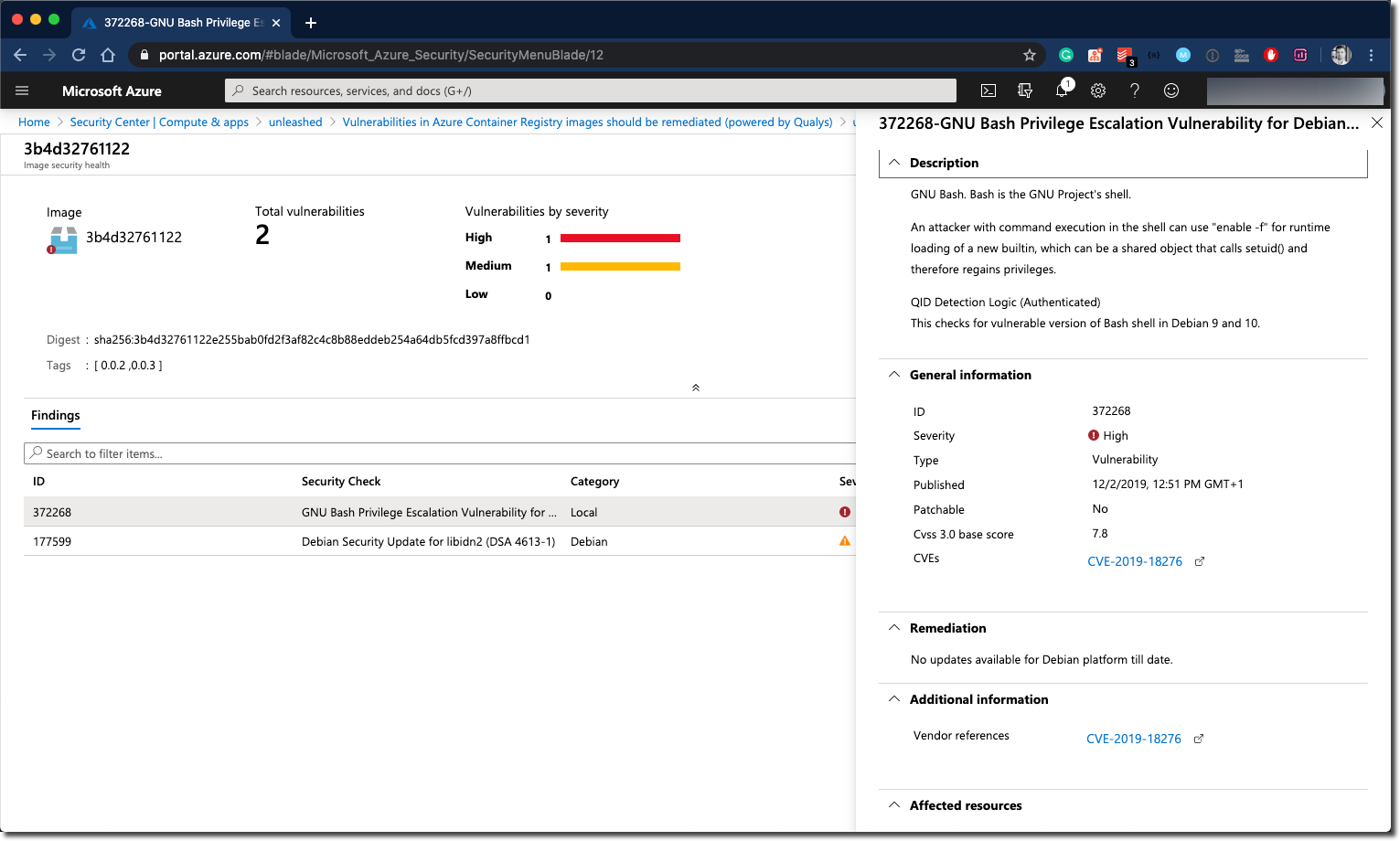
ASC provides a bunch of insights for containerized applications, and the possibility to drill through the data from different perspectives makes it powerful and assists you in the process of hardening your containers.
How Qualys Scans Your Docker Images
Every time you push a Docker image, it will be pulled and seamlessly executed with Qualys image scanner in a sandbox environment. The image scanner checks the current image for known vulnerabilities and security recommendations. If there are findings or recommendations, ASC will classify those and generate alerts for problems in the context of the image. If your image is safe and clean, ASC will not create alerts to minimize disruptions.
Windows Docker Image Scanning
ASC is relying on an external Docker image scanner offered by Qualys. At this point, Qualys’ scanner does not provide any Windows Container image scanning capabilities. That means you currently have no chance to get your Windows Docker Images scanned with ASC. Personally, this is just an additional reason why developers should migrate their Windows-based workloads to Linux containers using technologies like .NET Core instead of trying to stick with Windows for containerized application architectures.
Preview Features Worth Testing
Currently, ASC scans images once they are pushed to ACR. This is a great starting point. However, images with vulnerabilities or pending security recommendations can still be pulled and executed, which is still a risk. The ACR team is actively working on the Quarantine feature for ACR, which puts all new Docker Images into Quarantine. Although it is still in preview, you can already enable Quarantine for ACR manually. See quarantine docs in the ACR repository for further details. Once the Quarantine is generally available, the chances are good that we see seamless integration with ASC also on this level.
So you should watch the progress of ACR Quarantine.
Conclusion
You should use Azure Security Center to continuously monitor your entire Azure Subscription and all its resources to get detailed information about potential security vectors and threats.
Especially in the context of containerized application architectures, you should use ASC and get your Docker Images scanned once uploaded to ACR. Although you currently have to revisit the Security Center to get scanning results, it is still worth having this information at a know, central place.
The integration will shine once ACR Quarantine features are fully integrated into the workflow, which will prevent malicious images from being distributed.
Additionally, I would love to be able to select the actual image scanning service because we have seen different scanners finding different vulnerabilities. Perhaps we will be able to choose between services like Qualys and Aqua at some point in time.
The ACR Unleashed series
- Part 1 - Introduction and Geo Replication
- Part 2 - Authentication, IAM and Content Trust
- Part 3 - Integrate ACR and Azure Monitor
- Part 4 - Webhooks
- Part 5 - Tasks
- 👉🏻 Part 6 - Image scanning with Azure Security Center
- Part 7 - Use ACR as Registry for Helm charts
What Is Next
In the seventh and last part of ACR Unleashed, we will look into Helm chart support offered by Azure Container Registry.
You can also subscribe to my newsletter and get automatically notified when I publish articles here. That is the best way to stay current and never miss an article.